Infrastructure as Code (IaC) simplifies cloud management, but it introduces security risks if not properly handled. This article explores 13 tools that help secure IaC workflows by identifying vulnerabilities, enforcing policies, and ensuring compliance. These tools integrate into CI/CD pipelines, support multiple IaC formats, and work across major cloud platforms like AWS, Azure, and GCP. Here's what you need to know:
- Jit: DevSecOps platform with CI/CD integration and real-time cloud monitoring.
- KICS: Open-source tool with 2,400+ queries for static analysis.
- TFLint: Focuses on Terraform-specific linting and best practices.
- Prowler: AWS-focused security and compliance checks.
- Checkov: Multi-format support with 1,000+ built-in policies.
- Spectral: Developer-friendly scanner for secrets and misconfigurations.
- Trivy: Multi-purpose tool for IaC, containers, and dependencies.
- Terrascan: Policy-as-code enforcement using OPA.
- PingSafe: Broader cloud security posture management.
- CloudSploit: Continuous monitoring of live environments.
- Open Policy Agent (OPA): Customisable policy engine for IaC.
- Snyk: Developer-first security with Git and CI/CD integration.
These tools address vulnerabilities early, enforce compliance, and streamline cloud security. Below is a quick comparison.
Quick Comparison
| Tool | Focus | Supported IaC Formats | Cloud Platforms | Integration Options |
|---|---|---|---|---|
| Jit | DevSecOps automation | Terraform, CloudFormation, etc. | AWS, Azure, GCP | GitHub, GitLab, Jenkins |
| KICS | Static analysis | Terraform, Kubernetes, Ansible | AWS, Azure, GCP | CLI, CI/CD, IDE plugins |
| TFLint | Terraform-specific linting | Terraform only | AWS, Azure, GCP | CLI, GitHub Actions |
| Prowler | AWS security assessment | Terraform, CloudFormation | AWS | CLI, CI/CD pipelines |
| Checkov | Policy-as-code | Terraform, Kubernetes, Docker | AWS, Azure, GCP | CLI, IDE plugins, CI/CD |
| Spectral | Code security scanning | Terraform, CloudFormation, YAML | AWS, Azure, GCP | GitHub, GitLab, CI/CD |
| Trivy | Vulnerability scanning | Terraform, Kubernetes, Docker | AWS, Azure, GCP | CLI, CI/CD, container registries |
| Terrascan | Policy enforcement | Terraform, Kubernetes, Helm | AWS, Azure, GCP | CLI, CI/CD pipelines |
| PingSafe | Cloud security posture | Terraform, CloudFormation | AWS, Azure, GCP | API, SIEM tools |
| CloudSploit | Configuration scanning | Terraform, CloudFormation | AWS, Azure, GCP | CLI, API, web interface |
| OPA | Policy enforcement | Universal (JSON/YAML) | Cloud-agnostic | Kubernetes, CI/CD |
| Snyk | Developer-first security | Terraform, Kubernetes, Helm | AWS, Azure, GCP | CI/CD, IDE plugins, Git |
These tools enhance security, prevent misconfigurations, and integrate security into development workflows. Whether you're focused on Terraform-specific linting or multi-cloud compliance, there's a tool for your needs.
Security as Code - Incorporating Security into your IaC
1. Jit
Jit is a DevSecOps platform designed to strengthen Infrastructure as Code (IaC) security throughout the development lifecycle. Instead of just focusing on scanning infrastructure, it offers a broader scope, addressing security for code, cloud environments, and CI/CD pipelines [2].
Integration with CI/CD Pipelines
Jit simplifies security processes by automating tasks like SAST, SCA, and secrets scanning directly within CI/CD pipelines. Its AI-driven system prioritises alerts based on factors such as reachability and data sensitivity. Developers benefit from inline pull request checks that provide actionable suggestions for fixes. With seamless integration into platforms like GitHub and AWS, Jit ensures that security measures are woven into every stage of development [3][4].
Support for Multiple IaC Formats
Jit supports a wide range of IaC formats, making it versatile for different development environments. Compatible formats include Terraform, Pulumi, CloudFormation, AWS CDK, Kubernetes manifests, and Helm Charts. This flexibility allows for cloud-agnostic security analysis, catering to diverse deployment needs [5][6].
Cloud Platform Compatibility
Jit’s security features extend across major cloud platforms, including AWS, Azure, and GCP. Beyond static IaC scanning, the platform’s Cloud Security Posture Management actively monitors cloud infrastructure in real time. This helps organisations detect and address misconfigurations while maintaining consistent security practices across various environments [6].
Automated Policy Enforcement and Compliance Checks
Jit goes a step further by automating IaC, DAST, and SAST testing from a single interface. Its integration with tools like KICS enhances its ability to identify vulnerabilities and provides developers with clear, actionable insights. This empowers teams to implement security frameworks that align with their organisation's goals and requirements [3][4].
Next, explore KICS for more ways to improve IaC security.
2. KICS
KICS takes the concept of proactive security a step further by automating scans across various platforms. This open-source static code analysis tool is designed to identify security vulnerabilities, compliance issues, and misconfigurations early in the development process. With over 2,400 queries at its disposal, KICS offers extensive coverage, making it ready to use across multiple platforms without requiring additional configuration [7][9].
Support for Multiple IaC Formats
To ensure secure cloud configurations, KICS supports a wide range of Infrastructure as Code (IaC) formats, including Terraform, Kubernetes, Docker, AWS CloudFormation, Ansible, Helm, Google Deployment Manager, AWS SAM, Microsoft ARM, Microsoft Azure Blueprints, OpenAPI 2.0 and 3.0, Pulumi, Crossplane, Knative, and Serverless Framework [7].
For Terraform, KICS can scan .tf files, variable files, and plan outputs. It resolves variables using *.auto.tfvars files and default values, while users can also specify variable files via comments or the --terraform-vars-path flag [8].
Kubernetes manifests with .yaml extensions are fully supported. If Knative files are detected, Kubernetes Security Queries are automatically loaded. Additionally, the tool includes support for NIFCloud in Terraform files and offers specific queries for platforms like Databricks, NIFCloud, and TencentCloud [8][10].
Integration with CI/CD Pipelines
KICS integrates seamlessly into CI/CD pipelines, enabling continuous scanning of IaC with every update. This approach embeds security checks into the development process from the start [11][12][13].
For example, a demo showcased KICS automatically running scans on pull requests. The platform provides a centralised dashboard displaying real-time findings, allowing users to monitor the resolution process and take advantage of automated remediation workflows. In some cases, pull requests are automatically generated to fix detected issues [11].
Integrating KICS into your CI/CD pipeline ensures your infrastructure is continuously checked for vulnerabilities, reducing the risk of deploying insecure configurations.- Jonathan Rosenboim, Software Developer, Jit [11]
One example with Azure DevOps highlights KICS running as a Docker container, configured to fail pipelines if high-severity errors are detected [13].
Automated Policy Enforcement and Compliance Checks
KICS enables teams to enforce custom security policies, such as requiring bucket encryption or preventing the use of root Kubernetes pods. Pipelines are designed to fail if high-severity issues are identified, ensuring insecure configurations never make it to production [11][13].
The tool generates detailed reports in formats like JSON and SARIF, which categorise issues by severity and provide descriptions. These reports are accessible within CI/CD platforms, giving teams a clear view of their security status and compliance [12][13].
Cloud Platform Compatibility
KICS is compatible with major cloud platforms, including AWS, Azure, and GCP. It scans IaC templates, scripts, and configurations to identify vulnerabilities across infrastructure components such as web servers and databases [11].
A GitHub Actions workflow example demonstrates KICS running scans on every push or pull_request to the main branch. The workflow involves checking out code, setting up Docker, and executing the KICS scan command with the workspace directory mounted. This ensures continuous security checks across various cloud environments, reducing the likelihood of deploying insecure configurations [11].
Looking ahead, TFLint offers a more focused approach to Terraform validation, complementing KICS's broader scanning capabilities.
3. TFLint
TFLint is a dedicated linter for Terraform that goes beyond the built-in validators. It identifies errors, enforces best practices, and ensures code quality by analysing stylistic issues, security risks, outdated syntax, and unused declarations. This precise level of analysis makes TFLint an excellent addition to any Infrastructure-as-Code (IaC) security toolkit[14][15][18].
Cloud Platform Compatibility
TFLint boosts security across major cloud platforms by offering provider-specific plugins for AWS, Microsoft Azure, and Google Cloud Platform (GCP). These plugins dive deeper into security analysis, taking into account the unique characteristics and best practices of each platform[14][15][16][17][18]. By identifying provider-specific issues before deployment, TFLint helps catch potential vulnerabilities early in the process[14][15][16][18][19]. Each plugin is designed to align Terraform code with both general IaC standards and the specific security requirements of the respective cloud platform.
4. Prowler
Prowler is a security tool specifically designed for auditing AWS environments. It helps identify configuration issues and compliance gaps, producing detailed reports that enhance cloud security efforts.
AWS Compatibility
Built with AWS in mind, Prowler provides extensive coverage across services like EC2, S3, Lambda, and RDS. Its security checks ensure your AWS configurations follow established best practices, giving you peace of mind about your cloud setup.
Automated Compliance Checks
Prowler evaluates AWS configurations against well-known benchmarks, such as the CIS AWS Foundations Benchmark. It flags any deviations and offers clear guidance on how to fix them. With its detailed reports, security teams can prioritise and resolve issues more efficiently.
Integration with CI/CD Pipelines
Prowler fits smoothly into CI/CD workflows, running security checks during each deployment to catch vulnerabilities early. This proactive approach minimises the cost and disruption of fixing issues later in the development cycle.
Up next, learn about Checkov and its powerful scanning capabilities for improving IaC security.
5. Checkov
Checkov, an open-source security scanner from Bridgecrew, is a go-to tool for organisations managing diverse Infrastructure as Code (IaC) formats. Its ability to handle multiple cloud environments has made it a popular choice in the UK. By combining broad format compatibility with strong policy enforcement, Checkov helps enhance the security of IaC implementations.
Support for Multiple IaC Formats
One of Checkov’s standout features is its compatibility with a wide range of IaC formats. Whether you're working with Terraform, CloudFormation, Kubernetes (including Helm charts), ARM templates, Docker, or Ansible, Checkov has you covered. This flexibility is particularly useful for organisations operating in multi-cloud or hybrid setups. For example, if a company transitions from AWS to Azure, Checkov ensures security remains consistent by scanning both Terraform and ARM templates.
The tool is equipped with over 1,000 built-in policies, including those based on well-known frameworks like the CIS and AWS Foundations Benchmarks. This means organisations can start scanning their code immediately without the need to spend time creating custom rules.
Integration with CI/CD Pipelines
Checkov integrates smoothly with popular CI/CD platforms like Jenkins, GitHub Actions, GitLab CI, and Azure DevOps. Adding Checkov as a pipeline step allows teams to scan IaC files before deployment. For instance, a fintech company in the UK could configure GitHub Actions to run Checkov scans on every pull request, ensuring that only secure code makes it to production. This approach aligns with the shift-left security philosophy, addressing vulnerabilities early in the development process when they are simpler and less costly to fix.
Automated Policy Enforcement and Compliance Checks
With its extensive library of over 1,000 pre-set policies[20], Checkov automatically flags configurations that don’t meet security best practices or regulatory standards. This feature is particularly helpful for organisations needing to comply with UK-specific frameworks like GDPR or PCI DSS. For example, a healthcare provider in the UK integrated Checkov into its GitLab CI pipeline. This not only reduced the time spent on manual reviews by 60% but also ensured compliance with NHS data protection requirements.
Additionally, Checkov allows users to define custom policies in Python or YAML, enabling organisations to tailor the tool to their unique business needs and internal security standards.
Cloud Platform Compatibility
Checkov is compatible with all major cloud platforms, including AWS, Azure, and Google Cloud Platform. This ensures that organisations using multi-cloud or hybrid strategies can maintain consistent security controls. For example, a retail company operating across AWS and Azure can rely on Checkov to enforce uniform security measures, such as identifying publicly accessible storage buckets and providing actionable remediation steps.
Up next, we’ll take a closer look at Spectral and how it helps detect secrets and sensitive data within infrastructure code.
6. Spectral
Spectral, created by Check Point, is a security scanner tailored for developers. It combines various security functions into a single tool, helping organisations streamline their toolsets while maintaining strong security measures for their Infrastructure as Code (IaC) implementations.
Support for Multiple IaC Formats
Spectral supports major IaC formats like Terraform, CloudFormation, and Kubernetes manifests [23]. By directly analysing configuration files, it identifies misconfigurations and highlights the exact lines causing issues. Developers also receive targeted remediation suggestions, making it easier to understand not just what went wrong, but how to fix it [21][23]. This level of precision is particularly beneficial for teams managing multiple cloud environments, as it simplifies the learning process for security best practices and speeds up issue resolution.
Integration with CI/CD Pipelines
Spectral integrates effortlessly with CI/CD pipelines and cloud platforms, enabling automated IaC scans during routine build and deployment processes [21][3]. Its developer-focused design fits seamlessly into existing workflows, allowing teams to incorporate security checks without disrupting their processes. By automating these scans, Spectral ensures that security becomes a natural part of the development lifecycle.
Automated Policy Enforcement and Compliance Checks
One of Spectral's standout features is its centralised policy management. Organisations can customise the platform to align with their specific requirements [23], creating security policies that adhere to both industry standards and internal governance. This flexibility is particularly useful for UK businesses navigating strict regulatory requirements, enabling them to enforce compliance with ease.
Cloud Platform Compatibility
Spectral is compatible with all major cloud platforms, making it a great choice for organisations employing multi-cloud or hybrid strategies. For businesses managing complex cloud setups, Spectral offers free IaC asset scanning [22]. This allows UK organisations to test the tool's capabilities without an upfront financial commitment, helping them evaluate its suitability for their unique infrastructure and security demands.
Next, we’ll take a closer look at Trivy and its approach to vulnerability scanning for containers and infrastructure code.
7. Trivy
Trivy, an open-source vulnerability scanner developed by Aqua Security, is a versatile tool designed to handle security scans across containers, file systems, Git repositories, and Infrastructure as Code (IaC). Unlike tools that concentrate solely on IaC, Trivy offers a multi-functional security platform that consolidates these scans into a single, user-friendly interface.
By combining IaC checks with container and dependency scanning, Trivy delivers a well-rounded approach to maintaining cloud security.
Support for Multiple IaC Formats
Trivy supports a wide range of IaC formats, including Terraform, CloudFormation, Kubernetes manifests, Helm charts, and Docker Compose files. It also scans container images and application dependencies, all within one streamlined workflow. This unified approach eliminates the need to juggle multiple tools, allowing teams to pinpoint security vulnerabilities across their entire technology stack.
The scanner identifies misconfigurations in IaC templates, such as overly permissive IAM policies, unencrypted storage, or exposed databases. Its detection capabilities go beyond simple configuration checks, addressing policy violations and ensuring compliance with regulatory frameworks. This makes it especially useful for UK organisations that must adhere to stringent regulations.
Integration with CI/CD Pipelines
Trivy’s lightweight design makes it easy to integrate into CI/CD pipelines using Docker, GitHub Actions, or as a standalone binary. It produces JSON and SARIF outputs, ensuring compatibility with various CI/CD systems.
A standout feature is its customisable exit code settings, which let teams define pipeline failure criteria based on the severity of vulnerabilities. For instance, builds can be automatically blocked for high-severity issues, while medium or low-severity findings trigger warnings but don’t halt deployments. This flexibility helps organisations maintain a balance between security and development speed.
Cloud Platform Compatibility
Trivy works seamlessly across major cloud platforms, including AWS, Azure, and GCP, detecting platform-specific misconfigurations such as insecure S3 buckets, overly permissive Azure Storage accounts, or broad IAM bindings in GCP.
For businesses managing multi-cloud environments, Trivy’s consistent reporting format ensures uniform vulnerability assessments, regardless of the cloud provider. This feature simplifies security reporting and compliance tasks, particularly for UK organisations operating across different platforms.
Additionally, Trivy supports air-gapped environments, making it suitable for organisations with strict network isolation policies. By working with offline vulnerability databases, it ensures that scanning remains operational even in environments where internet access is restricted or unavailable.
Next, take a look at Terrascan for enforcing policy-as-code security in cloud infrastructures.
Need help optimizing your cloud costs?
Get expert advice on how to reduce your cloud expenses without sacrificing performance.
8. Terrascan
Terrascan is a policy-as-code scanner that leverages OPA (Open Policy Agent) and Rego to enforce security and compliance across a variety of cloud platforms and Infrastructure-as-Code (IaC) formats. It comes equipped with a library of over 500 built-in policies rooted in standards like CIS, NIST, and SOC2.
What makes Terrascan stand out is the tailored nature of its policies. Instead of offering generic templates, these policies are specifically designed for individual cloud providers and resource types. This allows for detailed and precise security checks that address specific misconfigurations often encountered in real-world scenarios.
Support for Multiple IaC Formats
Terrascan supports a wide range of IaC formats, including Terraform, CloudFormation, Kubernetes manifests, Helm charts, Kustomize configurations, and Dockerfiles. This versatility ensures that organisations can enforce consistent security practices across all their IaC workflows.
Its platform-agnostic design means teams can apply the same security policies regardless of the deployment method - whether it’s container orchestration with Kubernetes, provisioning infrastructure with Terraform, or managing resources through CloudFormation. This unified approach not only simplifies policy enforcement but also reduces the learning curve for security teams.
Automated Policy Enforcement and Compliance Checks
Terrascan automates the process of checking IaC templates against specific security rules. For example, it can verify configurations like AWS S3 bucket encryption or Azure resource group locks using Rego scripts and JSON-based rule files. By consolidating these standards, Terrascan helps streamline compliance management and reduces manual effort.
Cloud Platform Compatibility
Terrascan is designed to work seamlessly with AWS, Azure, and GCP, accounting for the unique characteristics of each platform. It understands details like AWS IAM structures, Azure Active Directory configurations, and GCP service account permissions, ensuring that security policies are applied consistently - even in multi-cloud environments.
Next, we’ll explore PingSafe and how it approaches cloud security posture management for IaC environments.
9. PingSafe
PingSafe earned the title of 'Best Tool for Comprehensive Cloud Security Beyond IaC' in 2025 [3]. This recognition underscores its ability to safeguard cloud environments beyond the usual Infrastructure as Code (IaC) scanning. It’s this broader functionality that helps PingSafe stand out in the cloud security space.
However, specifics about its IaC support and integrations haven’t been shared. Up next, let’s take a look at how CloudSploit handles automated cloud security assessments.
10. CloudSploit
CloudSploit is an open-source tool designed to uncover vulnerabilities in your cloud infrastructure. Unlike many Infrastructure as Code (IaC) scanners that focus solely on pre-deployment code reviews, CloudSploit takes it a step further by continuously monitoring your active cloud environment for misconfigurations.
Cloud Platform Compatibility
CloudSploit works particularly well with Amazon Web Services (AWS), offering checks for services like EC2, S3, RDS, IAM, and VPC. While it also supports other major providers like Azure and Google Cloud Platform, its AWS integration is the most comprehensive, with a broader range of checks available.
This multi-platform support ensures that critical cloud services are under constant surveillance, helping teams stay on top of potential risks.
Continuous Monitoring and Reporting
The tool scans for issues such as unencrypted storage buckets, overly permissive security groups, and weak IAM policies. It produces detailed reports, helping teams prioritise fixes by assigning risk levels and providing clear, actionable remediation steps.
What makes CloudSploit stand out is its focus on real-time scanning of live environments rather than just analysing code before deployment. This allows it to detect configuration drift and respond to new security risks as they arise, offering an additional layer of protection beyond traditional IaC tools.
Next, let’s explore how SentinelOne tackles endpoint security in cloud environments.
11. SentinelOne
SentinelOne offers its Singularity CNAPP to safeguard your entire cloud infrastructure, including Infrastructure as Code (IaC) deployments [1].
Cloud Platform Compatibility
The Singularity CNAPP is designed to work seamlessly across multi-cloud environments - whether public, private, or hybrid. This ensures your IaC deployments are protected across all major cloud providers.
Next, we’ll dive into Open Policy Agent’s flexible approach to policy management for IaC.
12. Open Policy Agent (OPA)
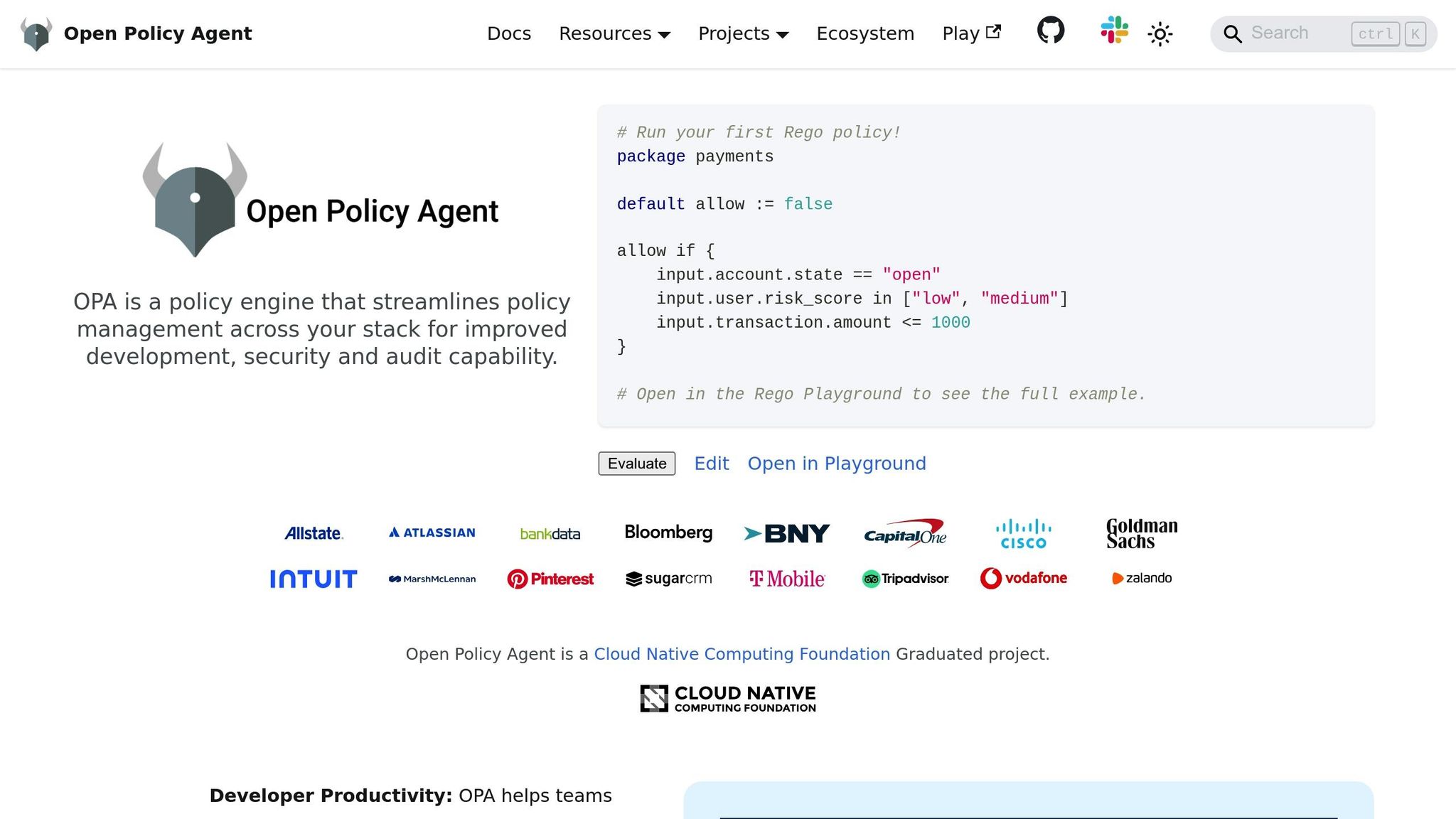
Open Policy Agent (OPA) is a policy engine designed to bring flexible, code-driven policy management into your Infrastructure as Code (IaC) workflows. Unlike traditional tools that rely on predefined rules, OPA allows you to create tailored policies using its Rego language, offering a high degree of customisation.
Broad Support for IaC Formats
One of OPA's key strengths is its ability to work with multiple formats. It supports Terraform, Kubernetes, CloudFormation, and Docker, enabling you to apply consistent security policies across your infrastructure, no matter which IaC tools your teams prefer.
For additional functionality, the Conftest project builds on OPA's capabilities, giving you the tools to validate Terraform plans, Kubernetes YAML files, and other configurations against your custom policies before deployment.
Seamless CI/CD Integration
OPA fits effortlessly into your CI/CD pipelines with its command-line interface and REST API. It integrates with tools like Jenkins, GitLab CI, and GitHub Actions, enabling rapid validation of every change in just milliseconds.
Automated Compliance and Policy Checks
OPA streamlines compliance by automating checks for standards such as SOC 2, PCI DSS, and GDPR. It continuously evaluates configurations, flagging any violations before they can affect your production systems.
The decision logging feature offers detailed audit trails for all policy decisions, simplifying compliance reporting during audits and regulatory reviews.
Compatible Across Cloud Platforms
OPA is a cloud-neutral solution, designed to work seamlessly with AWS, Microsoft Azure, Google Cloud Platform, and hybrid environments. It doesn’t rely on specific cloud provider APIs, making it an ideal choice for organisations managing multi-cloud setups.
Whether you're working with AWS IAM policies, Azure Resource Manager templates, or Google Cloud Deployment Manager configurations, OPA ensures consistent policy enforcement across all platforms. Its unified policy language provides a cohesive approach to security, preparing your infrastructure for the next step in developer-centric scanning.
Up next, we’ll explore how Snyk takes a developer-first approach to IaC security scanning.
13. Snyk
Snyk takes a developer-first approach to Infrastructure as Code (IaC) security, embedding security checks directly into developers' workflows. This focus ensures that security becomes an integral part of the development process rather than a roadblock. As part of its comprehensive security platform, Snyk IaC equips development teams with the tools they need to identify and address vulnerabilities efficiently.
The acquisition of Fugue, the creators of Regula, has bolstered Snyk's capabilities in policy enforcement across cloud environments, further enhancing its offering [23].
Support for Multiple IaC Formats
Snyk IaC supports a wide range of IaC formats, including Terraform (single files and modules), AWS CloudFormation, Azure Resource Manager (ARM), Kubernetes Manifests, and Helm Charts [24][25][26][27][28]. This extensive compatibility ensures that teams can maintain consistent security practices, regardless of the tools they use.
In addition to these formats, Snyk also supports AWS CDK files, Kustomize configurations, and Serverless framework files, offering even greater flexibility for development teams [25][26][27][28].
Integration with CI/CD Pipelines
Snyk integrates seamlessly with popular CI/CD tools like Jenkins, CircleCI, GitHub Actions, AWS CodePipeline, Azure Pipelines, Bitbucket Pipelines, Maven, TeamCity, and GitLab [29][30][32]. These integrations allow for automated scanning at key stages of development - both before and after merging - ensuring that vulnerable configurations are caught early, before they can make their way into production.
With its CLI and CI/CD tool integrations, Snyk provides clear vulnerability reports and actionable fix recommendations. Developers can also benefit from IDE plugins, which deliver real-time security feedback directly within their coding environments. Additionally, Git-based pull request checks include one-click fixes, making it easier to resolve issues efficiently [29][30][2].
Automated Policy Enforcement and Compliance Checks
Snyk automates compliance checks while keeping developers at the centre of the process. The platform includes built-in security rules and supports custom policies tailored to organisational needs. By scanning for vulnerabilities across code, open-source dependencies, containers, and infrastructure configurations, Snyk ensures that compliance is managed seamlessly within CI/CD pipelines [29][31][32].
Snyk also provides developer-friendly remediation guidance and continuously monitors for new vulnerabilities, alerting teams as issues arise. Its policy enforcement capabilities help organisations maintain compliance with minimal manual effort, reducing the burden of meeting regulatory requirements. This approach aligns with Snyk's emphasis on flexibility and adaptability across different environments [32].
Cloud Platform Compatibility
Snyk IaC delivers cloud-neutral security coverage across AWS, Microsoft Azure, and Google Cloud Platform, making it an excellent choice for organisations operating in hybrid or multi-cloud setups [25][26][27][28].
The platform uses context-aware rules to minimise false positives by considering the specific cloud environment and configuration. This ensures that alerts are relevant and actionable, helping development teams focus on the most pressing issues. This level of intelligence sets Snyk apart from tools that rely solely on pattern matching without factoring in the deployment context [23].
With consistent security validation across all major cloud platforms, Snyk helps teams maintain unified security standards, no matter their cloud strategy.
Tool Comparison Table
Selecting the right Infrastructure as Code (IaC) security tool boils down to your specific needs and workflows. To make the decision easier, here's a detailed comparison of key tools, their features, and strengths.
| Tool | Primary Focus | Supported IaC Formats | Cloud Platforms | Integration Options | Key Strengths |
|---|---|---|---|---|---|
| Jit | DevSecOps automation | Terraform, CloudFormation, Kubernetes | AWS, Azure, GCP | GitHub, GitLab, Jenkins, CI/CD pipelines | Automated security orchestration |
| KICS | Static analysis | Terraform, CloudFormation, ARM, Kubernetes, Helm, Ansible | AWS, Azure, GCP, Alibaba Cloud | CLI, CI/CD integration, IDE plugins | Open source, broad rule coverage |
| TFLint | Terraform-specific linting | Terraform only | AWS, Azure, GCP | CLI, GitHub Actions, pre-commit hooks | Deep Terraform expertise, plugin architecture |
| Prowler | AWS security assessment | CloudFormation, Terraform (AWS focus) | AWS primarily | CLI, CI/CD pipelines, automation scripts | AWS compliance checks |
| Checkov | Policy-as-code | Terraform, CloudFormation, ARM, Kubernetes, Helm, Dockerfile | AWS, Azure, GCP | CLI, IDE plugins, CI/CD integration | Extensive policy library, multi-format support |
| Spectral | Code security scanning | Terraform, CloudFormation, Kubernetes, YAML | AWS, Azure, GCP | GitHub, GitLab, CI/CD pipelines | Developer-friendly interface |
| Trivy | Vulnerability scanning | Terraform, CloudFormation, Kubernetes, Dockerfile | AWS, Azure, GCP | CLI, CI/CD integration, container registries | Lightweight, multi-purpose security scanner |
| Terrascan | Static code analysis | Terraform, CloudFormation, ARM, Kubernetes, Helm | AWS, Azure, GCP | CLI, CI/CD pipelines, admission controllers | Flexible policy engine, compliance frameworks |
| PingSafe | Cloud security posture | Terraform, CloudFormation, ARM | AWS, Azure, GCP | API integration, SIEM tools, dashboards | Real-time monitoring, threat detection |
| CloudSploit | Configuration scanning | CloudFormation, Terraform | AWS, Azure, GCP, Oracle Cloud | CLI, web interface, API | Simple deployment, clear reporting |
| Open Policy Agent | Policy enforcement | Universal (JSON/YAML) | Cloud-agnostic | Kubernetes, service meshes, CI/CD | Flexible policy language, ecosystem integration |
| Snyk | Developer-first security | Terraform, CloudFormation, ARM, Kubernetes, Helm | AWS, Azure, GCP | CI/CD, IDE plugins, Git integration | Seamless developer workflow integration |
When narrowing down your options, keep these aspects in mind:
- Integration Options: Tools like Snyk shine in developer-centric workflows, while Checkov and KICS excel in CI/CD pipelines. These features align well with multi-cloud strategies.
- Cloud Platform Support: Most tools support major platforms like AWS, Azure, and GCP. However, some, like Prowler, focus specifically on AWS.
- User Experience: Command-line tools such as TFLint and Trivy offer precise control but require technical expertise, whereas platform-based solutions like Spectral provide a more user-friendly approach.
- Scalability: Enterprise-grade tools like Snyk are designed to scale with your organisation, while lightweight options like Trivy and CloudSploit are better suited for smaller teams or niche use cases.
- Support and Maintenance: Open-source tools often demand more hands-on management, while commercial solutions usually come with dedicated support and managed services.
The right tool doesn’t just secure your infrastructure - it can also streamline and enhance your overall DevOps workflow. Use this comparison to identify the tool that aligns best with your organisation's goals and technical capabilities.
Conclusion
As highlighted throughout this guide, the tools discussed play a key role in enabling secure and compliant cloud operations. For UK organisations navigating the complexities of the cloud environment, Infrastructure as Code security tools are more than just helpful - they're essential. From Terraform-focused linting with TFLint to robust policy enforcement using Open Policy Agent, these tools offer a diverse range of solutions for safeguarding cloud configurations.
Proactively securing cloud setups is critical, and tools like Prowler and Checkov excel at identifying misconfigurations and ensuring compliance. The availability of open-source options also provides a cost-effective way for UK businesses to enhance their cloud security without the burden of hefty licensing fees.
The ability to integrate these tools into existing workflows transforms security from a potential hurdle into an enabler of efficiency. Solutions such as Snyk and Spectral simplify the path from code development to production deployment, aligning security with the fast-paced demands of modern cloud strategies.
For organisations adopting multi-cloud approaches, flexibility is key. Tools like Terrascan and Checkov, which support multiple platforms such as AWS, Azure, and Google Cloud, offer the adaptability needed to optimise cloud usage based on factors like cost, compliance requirements, and functionality.
The shift towards developer-centric security is also reshaping the landscape. Tools like Jit and Snyk bring security checks directly into the development process, embedding secure coding practices into everyday workflows. This approach not only strengthens security but also aligns with the agile methodologies many UK organisations are embracing.
For those seeking expert guidance, Hokstad Consulting provides tailored support in DevOps transformation and cloud cost engineering, helping businesses implement these tools as part of a broader infrastructure strategy.
The tools outlined in this guide lay the groundwork for secure, compliant, and efficient cloud operations. By selecting and integrating the right solutions for your organisation's needs, you can build a unified security strategy that supports both innovation and resilience.
FAQs
What should I consider when selecting the best IaC security tool for my cloud environment?
When selecting an Infrastructure as Code (IaC) security tool, it's crucial to evaluate how well it suits your specific cloud environment. Consider the cloud provider you use - whether it’s AWS, Azure, or GCP - along with your organisation's security requirements and the tool’s compatibility with your existing DevOps workflows.
A standout feature to prioritise is proactive security scanning. By identifying vulnerabilities before deployment, this functionality helps address issues early, reinforcing your security measures from the outset.
Additionally, choose a tool that aligns with your cloud provider and offers a robust set of features, such as automated configuration checks, vulnerability detection, and smooth integration with CI/CD pipelines. Opting for a solution that fits seamlessly into your workflows and supports your security objectives will ensure a safer and more efficient cloud infrastructure.
What are the main differences between open-source and commercial IaC security tools?
Open-source IaC security tools are freely available and come with access to their source code, which allows users to customise them to fit specific needs. They also benefit from the backing of a global community for troubleshooting and updates. However, these tools might fall short when it comes to features like automated prioritisation or effective filtering of false positives, and they typically don't offer dedicated vendor support.
On the other hand, commercial IaC security tools often come packed with extra features such as automated issue prioritisation, advanced filtering options, and dedicated support from the vendor. These capabilities can simplify security management, enhance reliability, and save valuable time - particularly for organisations managing complex or large-scale cloud infrastructures.
How does using IaC security tools in CI/CD pipelines improve organisational security?
Integrating Infrastructure as Code (IaC) security tools into your CI/CD pipeline is a smart way to catch vulnerabilities early in the development process. This method, known as 'shifting security left', ensures that potential issues are spotted and fixed well before they make it to production.
By automating security checks and enforcing compliance policies throughout the pipeline, these tools minimise human error, simplify secure deployments, and ensure consistent cloud configurations. The result? Stronger security, faster development cycles, and significant savings in both time and resources.
